This Defcon I’m stuck at home as are others, so Av1d, speexvocon, wagwan_piffting_blud and I formed a team to play the Project Mammoth Challenge.
Challenge #1 Metadata FTW!

This one was pretty easy, just look at the metadata to get the key. Fired up Audacity and Edit -> Metadata:

Challenge #2 All your base64

This one just required looking at the exifdata, which av1d did:

I base64 decode it and sure enough:
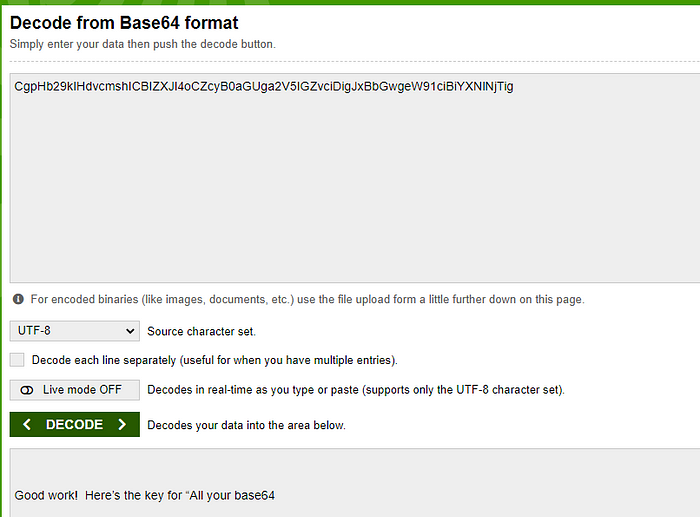
At this point we only had a snippet and we solved another puzzle first, but I went back to av1d and had him spill the whole thing.

Speex also found this puzzle by running strings:

Challenge #3 Hello World

This one we got speex help on, he used winrar to just name the file a .zip and repair it, inside the zip file was a hello-world directory with the key.

Challenge #4 What the DTMF?

This one was pretty straight forward, in the beginning of the MP3 when you play it there’s a phone dial tone followed by very fast touch tones, I luckily have a DTMF decoder already on Audacity so this was easy.


The only thing that kind of stumped us on this is there is one digit that decodes as a # symbol that the challenge makers inexplicitly just decided to make an F for no apparent reason whatsoever, but being hex it had to be either an E or an F.
Challenge #5 Dot dot dash


This one was pretty easy conceptionally, the youtube link goes to a video of two buddies playing guitar over the phone to pound out morse code dots and dashes, and the Mp3 dot-dot-dash.mp3 in the zip archive was just that only with drums. However it took forever to get it right and get the key. Spectrum Analyzer helped:

Challenge #6 Lazy Admin

To be honest this one pissed me off, essentially you just dial the 415 number, hit 9 for admin from the IVR and the password is ADMIN (23646) on the keypad. As a phone phreak I have NEVER ran across any PBX, phone equipment or voicemail etc that used ADMIN spelled out on the DTMF keypad as a ‘default’ password. The youtube link in this one is a Hackers movie clip red herring that makes you think the password will be GOD or at least LOVE, SECRET or SEX. Ugh tried several defaults before getting this one from our team member wagwan.
Challenge #7 Simon Says

This one’s fairly straight forward if you’ve played telechallenge before, the phone system sends a DTMF, you have to guess what it is, then it progresses, so for example phone system sent an 8, then you guess 8, then it sends an 83, you press 83 and it progresses to 835, etc until you get 83501952. I used to be good at decoding DTMF by ear, but I just brute forced it. After I got the key I was kind of pissed that you had to submit this one with {DialedUpCTF} as the What the DTMF didn’t require that (and we solved all these out of order), seems like they all should require it or optionally ignore it on all but hey whatever.
Challenge #8 Spectralicous

For this one you have to grab a modified version of the original mp3 from the spectralicious folder

Then looking at it under spectrum analyzer you’ll see something like this:
Sign language, decode for key.
Challenge #9 Stego-saurus

For this one you had to check program changes in the midi, we used avid sibelius to get this:
Then decode to binary like this:
Challenge #10 That’s completely notes!

For this one you had to work off 2 files in the archive, an mp3 and png

The PNG was the notes you needed to convert to binary:

Then from the mp3 in the folder you hear redbox tones of 3 quarters, a dime and a nickle which adds up to 90 cents. You needed to XOR the binary with 90 to get the flag:

And that’s all she wrote, this was a great little mini CTF.
